Controlla il gioco. Sceglici come tuo IT partner
La partita più impegnativa da giocare è restare al passo con la trasformazione digitale.
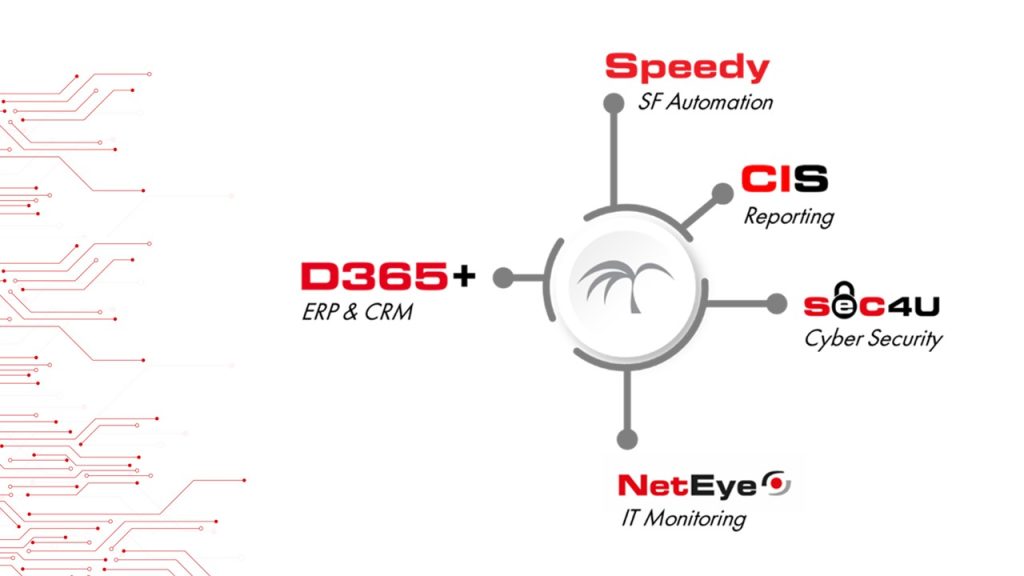
D365+
Business Applications
Gestisci i processi aziendali in modo più efficiente, migliora la produttività e promuovi la collaborazione tra dipartimenti.
NETEYE
IT Systems Management
Monitora e gestisci in modo olistico e automatico l’intero ambiente IT per avere tutto sotto controllo in minor tempo.
SEC4U
Cyber Security
Proteggi i dati aziendali da minacce esterne, sfruttando il punto di vista difensivo e offensivo degli esperti di sicurezza.
Project Management Solutions
Service Management
Migliora l’efficienza, l’affidabilità e la qualità dei servizi IT con una soluzione in grado di soddisfare sia gli utenti sia la clientela!
Affronta la sfida con un compagno di squadra pronto a supportarti
nell’analisi dei processi, nella scelta degli strumenti ideali, nell’implementazione dei cambiamenti più significativi per il tuo business e…vinci la partita!🏆
…more than software,
your IT partner
Appassionati di tecnologia, scendiamo in campo per supportare la crescita e il benessere delle aziende con soluzioni di Enterprise Resource Planning (ERP), Customer Relationship Management (CRM), Business Intelligence, Sales Force Automation, IT Systems Management, Service Management e Cyber Security.
I servizi di consulenza, project management, supporto, sviluppo software, system integration e formazione fanno parte del nostro schema di gioco.
Le soluzioni IT pensate e create negli anni per supportare la digital transformation sono il nostro punto di forza.

SETTORI DI APPLICAZIONE
Il miglioramento dell’efficienza operativa, la gestione ottimizzata delle risorse, l’aumento della produttività e l’ottimizzazione dei processi sono aspetti fondamentali per tutti i settori industriali senza eccezioni. Tuttavia, riconosciamo che ogni settore ha le proprie peculiarità.
Enterprise
Accelera la crescita della tua azienda attraverso l’automazione e la digitalizzazione dei processi

Fashion
Unisci l’arte, la passione, l’eleganza dei tessuti al digitale per il successo sostenibile della tua azienda di moda
Commercio all’ingrosso
Incrementa l’efficienza operativa del tuo magazzino e ottimizza le tempistiche di distribuzione

Manifatturiero
Trasforma e ottimizza i processi produttivi del tuo business con il digitale
I NOSTRI PARTNER
La sinergia con gli specialisti del settore ci consente di offrire soluzioni complete e di alta qualità, mantenendo sempre il passo con le ultime innovazioni tecnologiche
I NOSTRI PARTNER
I NOSTRI CLIENTI








































































BLOG POST
VUOI METTERTI IN GIOCO
CON LE NOSTRE SOLUZIONI?
Siamo pronti ad affiancarti per ottenere il massimo dalle tue risorse, ottimizzare i processi aziendali ed eccellere nel mercato. Fai Touchdown!






